SCEP Enrollment Service
SCEP is a PKI communication protocol which utilizes PKCS#7 and PKCS#10 messages that are sent over Hypertext Transfer Protocol (HTTP).
It is the most widely deployed protocol for certificate requests and CRL queries. However, the protocol does not support certain certificate management features such as in-band certificate revocation transactions.
To support more comprehensive functionality the IETF protocol suite provides two other certificate
management protocols – CMP and CMC.
SCEP is not a formal standard or RFC; it is a draft which has already expired and has been published as
historic. The protocol supports operations such as public key distribution through CA and RA, certificate enrollment, certificate query and CRLquery.
Its main characteristics are:
- Request/response model based on HTTP (GET method; optional support for POST method)
- Only supports RSA-based cryptography
- Uses PKCS#10 as the certificate request format
- Uses PKCS#7 in order to convey cryptographically signed/encrypted messages
- Supports asynchronous granting by the server, with regular polling by the requester
- Has limited Certificate Revocation List (CRL) retrieval support (the preferred method is through a CRL Distribution Point (CDP) query, for scalability reasons)
- Does not support online certificate revocation (must be done offline through other means)
- Requires the use of a challenge password field within the Certificate Signing Request (CSR), which must be shared only between the server and the requester
SCEP is described in the RFC 8894
The service download the CA certificates storing them in the selected KeystoreService with the alias prefix scep-cacerts_.
The generated private KeyPair will be stored in the selected KeystoreService with the alias sce-request-key-pair.
The signed certificate received from the SCEP server will be stored in the KeystoreService with the alias scep-enrolled-key-pair.
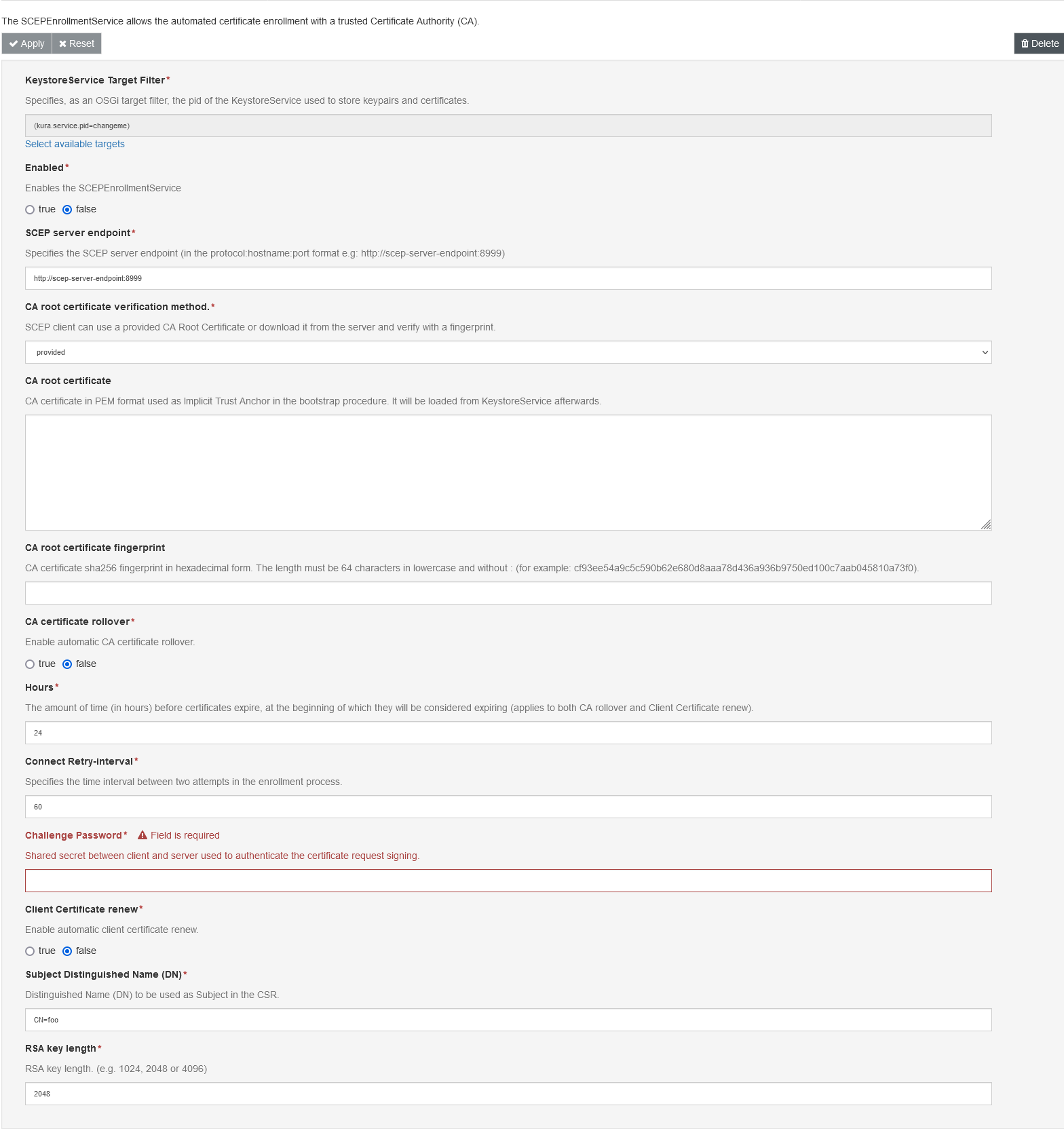
The SCEPEnrollmentService component can be configured with the following attributes:
-
KeystoreService Target Filter:Specifies, as an OSGi target filter, the pid of the KeystoreService used to store keypairs and certificates.
-
Enabled:Enables the SCEPEnrollmentService.
-
SCEP server endpoint:Specifies the SCEP server endpoint (in the protocol:hostname:port format e.g: http://scep-server-endpoint:8999).[1]
-
CA root certificate verification method.:SCEP client can use a provided CA Root Certificate or download it from the server and verify with a fingerprint.
-
CA root certificate:CA certificate in PEM format used as Implicit Trust Anchor in the bootstrap procedure. It will be loaded from KeystoreService afterwards.[1]
-
CA root certificate fingerprint:CA certificate sha256 fingerprint in hexadecimal form. The length must be 64 characters in lowercase and without : (for example: cf93ee54a9c5c590b62e680d8aaa78d436a936b9750ed100c7aab045810a73f0).[1]
-
CA certificate rollover:Enable automatic CA certificate rollover. By default the check on certificate velidity is done every 24 hours.
-
Certificate expiration check time: The amount of time (in hours) before expiration when the certificates or CA check are performed.
-
Connect Retry-interval:Specifies the time interval between two attempts in the enrollment process..
-
Challenge Password:Shared secret between client and server used to authenticate the certificate request signing..
-
Client Certificate renew:Enable automatic client certificate renew. By default the check on certificate validity is done every 24 hours.
-
Subject Distinguished Name (DN):Distinguished Name (DN) to be used as Subject in the CSR.
-
RSA key length:RSA key length (e.g. 1024, 2048 or 4096). By defaul 2048 bits.
Certificate renewal
The SCEP Enrollment Service is able to automatically renew the client certificate.
If the Client Certificate renew is set to true, starting from the amount of time (defined by the property Certificate expiration check time) before the certification expiration instant, the service will start the process to renew the certificate using the previous Keypair and the same Subject Distinguished Name (DN).
[1] A change in this property triggers a new client bootstrap with a subsequent enrollment
Updated 4 months ago
