Bundle Signing
Before switching ESF to production mode, application bundles developed by customers must be signed.
ESF bundles are already signed by Eurotech and do not require to be signed by the customer.
Certificate Generation
Public Key Infrastructure (PKI) certificates can be created in different ways:
-
Self-signing the public key (self-signed certificate)
-
Signing the public key with a company's certificate chain
-
Sending a Certificate Signing Request (CSR) to a trusted Certificate Authority (CA)
For code signing the first two options are inexpensive. Most of the times a self-signed certificate is just enough to get started.
Self-signed Certificate
A public/private key pair and the associated self-signed certificate can be created using the keytool command-line utility. This utility is available, free of charge, from any Java Development Kit (Oracle JDK, OpenJDK etc) for all operating systems.
The example below makes use of ${} to denote a placeholder that will be replaced by an actual value. The notation is the same used in shell scripts to expand the variable between braces.
For example ${keystore_file} can be replaced by BundleSigningKeystore.ks.Please note that the generated keystore contains the private key used to sign your code.
The keystore and the private key are protected by passwords (see below).
Keep these passwords and the keystore in a safe place.
- Use keytool to generate a keystore containing the new public/private key pair and the associated self-signed certificate:
# Note: key_pass and keystore_pass are respectively the password of the keystore
# and the password of the private key.
# Keep these passwords and the keystore in a safe place.
keytool -genkey -noprompt -trustcacerts -keyalg RSA -keysize 2048 \
-alias ${cert_alias} -dname ${dn_name} -keypass ${key_pass} \
-keystore ${keystore_file} -storepass ${keystore_pass} \
-validity ${cert_validity_days}where:
- ${cert_alias} is the alias for the new certificate.
- ${dn_name} is the Distinguished Name of the new certificate (see below).
- ${key_pass} is the password to be set for the new certificate.
- ${keystore_file} is the filename of the new keystore.
- ${keystore_pass} is the password to be set for the new keystore.
A valid Distinguished Name (dn_name) can be the following:
CN=www.companyname.com,O=Company Name,C=USCommas (,), quotation marks (") and semicolons (;) appearing in the certificate Distinguished Name (DN) must be escaped using the backslash (\) character.
- Optionally, check that the newly created certificate is in the keystore:
keytool -list -v -alias ${cert_alias} -keystore ${keystore_file}Import the Certificate in ESF
The certificate that will be used to verify the bundles signature must be first imported in the ESF keystore. The location of the ESF keystore in the gateway filesystem is /opt/eurotech/esf/user/security/.certificates.ks.
There are two ways the bundle signing certificate can be added to ESF:
- At any time from the Security menu of the Everyware Gateway Administration Console Web UI
- Before the very first ESF boot adding it manually to the ESF keystore.
Continuing the example of the previous section, the bundle signing certificate must be first exported by the bundle signing keystore:
# Note: the certificate will be exported to the file denoted by cert.file.
# The certificate is public and does not contain any secret.
# You will need the password of the keystore and the password of the private key.
keytool -export -v -keystore ${keystore_file} -alias ${cert_alias} \
-file ${cert_file} -storepass ${keystore_pass} -keypass ${key_pass}Import the Certificate from the Administration Console
This method can be used at any time to quickly add a bundle signing certificate to ESF.
The certificate exported in the previous section is in DER format, while the Administration Console only accepts certificates in PEM format.
The exported certificate can be converted using the openssl utility:
openssl x509 -inform der -in ${cert_file} -out ${cert_file_pem}The certificate (in PEM format) can then be added to the ESF keystore from Security | Certificates List in the Administration Console:
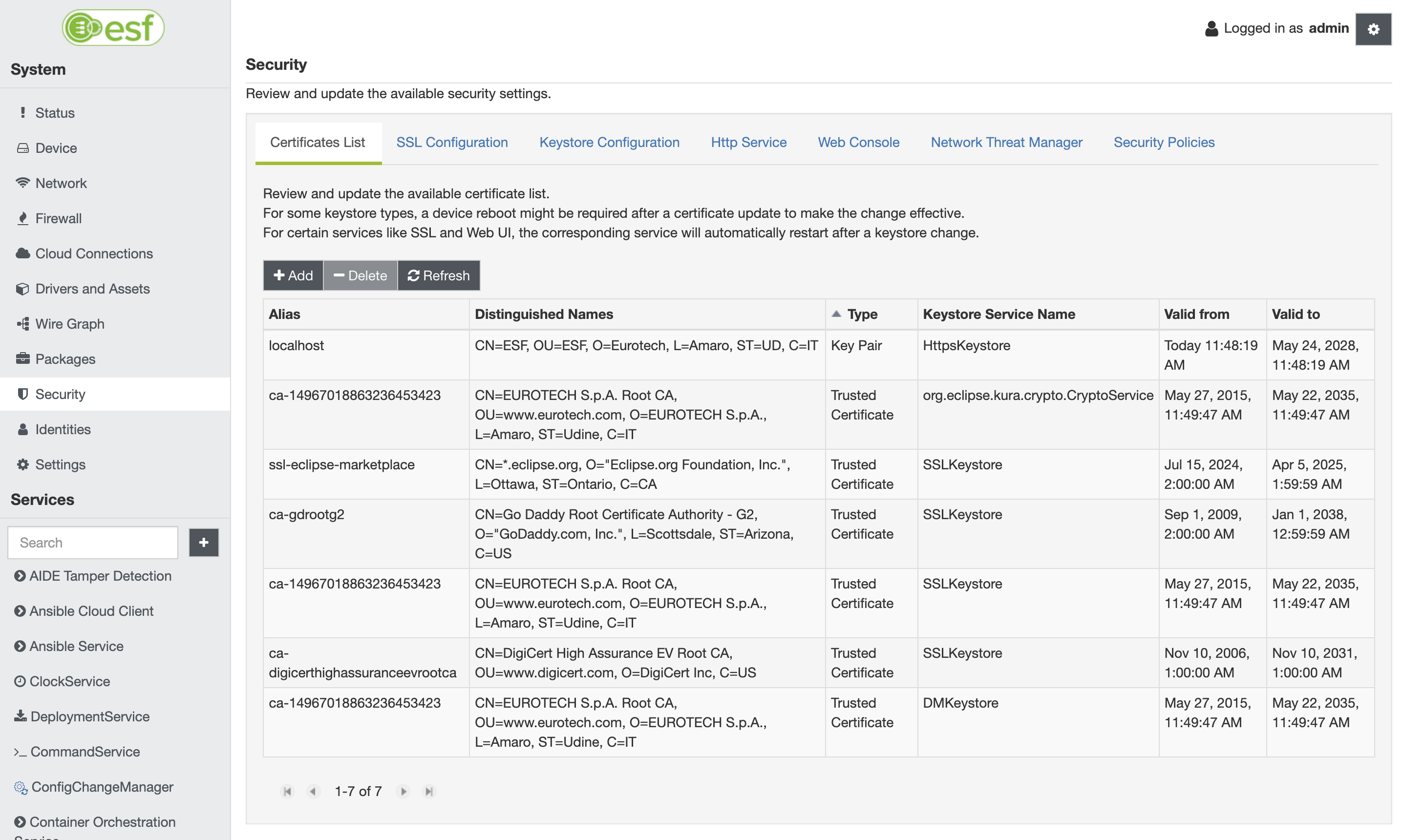
By clicking on Add, select Certificate as type of entry. Select the org.eclipse.kura.crypto.CryptoService keystore, specifying the Storage Alias and the PEM Certificate for the keypair used to sign the customer bundles.
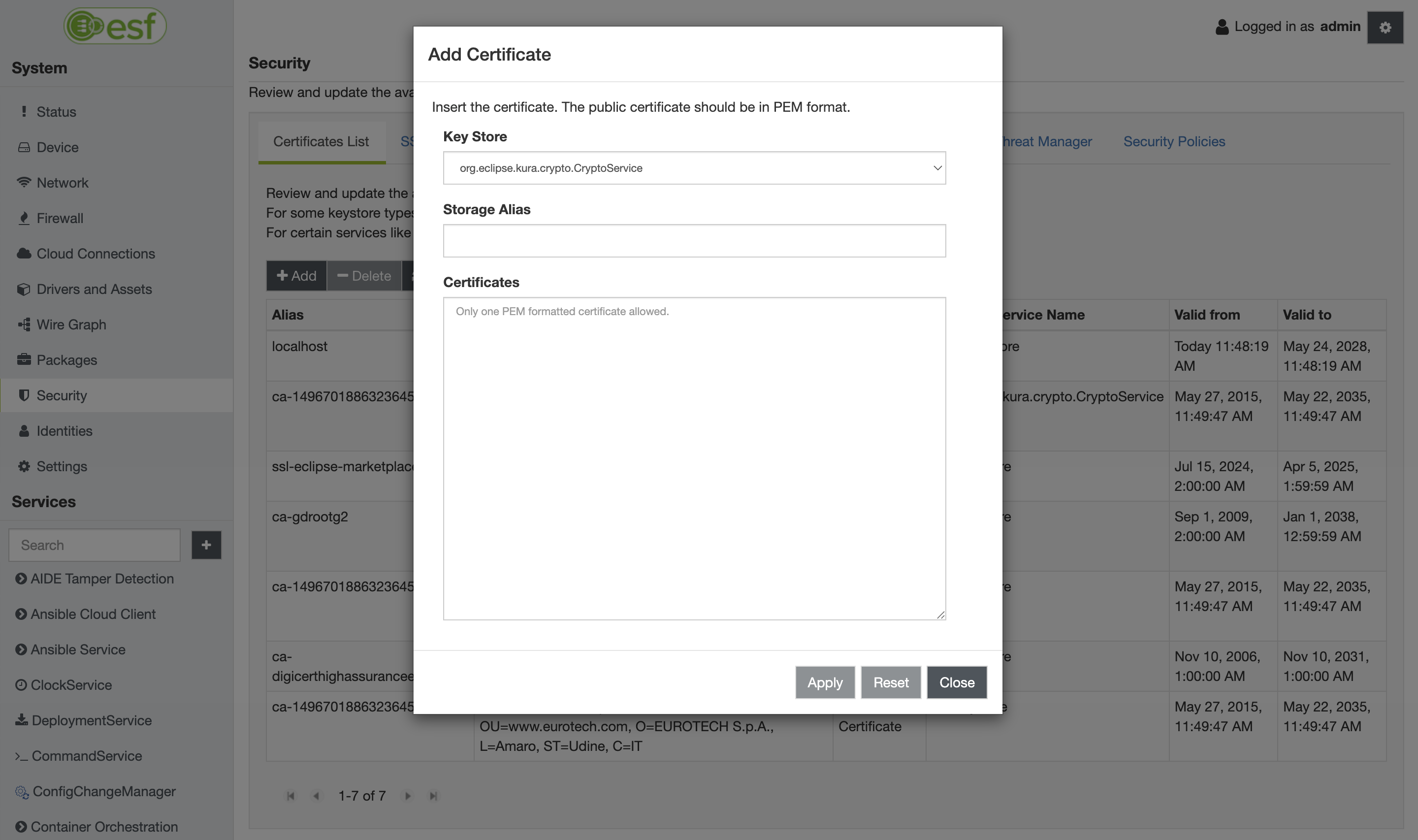
Once added, the new certificate will be listed in the Certificates List.
Import the Certificate Directly in the ESF Keystore
The bundle signing certificate can be directly imported in a keystore that will replace the ESF factory keystore located at /opt/eurotech/esf/user/security/.certificates.ks on the gateway filesystem.
This can be done only before the very first ESF boot regardless whether ESF is running in development or production mode.
If the ESF keystore located at /opt/eurotech/esf/user/security/.certificates.ks is replaced after the very first boot, ESF will detect that the keystore has been tampered and will refuse to boot.
For security reasons, the ESF factory keystore located at /opt/eurotech/esf/user/security/.certificates.ks is protected by an initial password which is not disclosed to customers. Due to this restriction, customers cannot directly import their certificates to the ESF factory keystore.
Eurotech provides an equivalent keystore, whose password is changeit, containing the Eurotech certificates needed to verify the signature of the ESF runtime.
This keystore can be downloaded from this link.
The customer can import his own certificates in this keystore and replace the ESF factory keystore located in /opt/eurotech/esf/user/security/.certificates.ks.
the value of the initial keystore password is written in plain text in the value of the kura.keystore.password property in /opt/eurotech/esf/framework/kura.properties. For improved security it is advisable to change the initial keystore password and modify the kura.keystore.password accordingly.
Having the keystore password stored in plain text in the kura.properties file represents a momentary vulnerability where the keystore could be tampered by an attacker before the very first ESF boot. For improved security it is advisable to boot ESF once before shipping the gateway.
In all cases, ESF will change the initial keystore password to a randomly generated password at the very first boot. The new password is securely stored and cannot be recovered.
Continuing the example, the certificate exported from the the bundle signing keystore can be imported in another keystore with:
# Note: certificates.ks is the name of the keystore downloadable from
# https://s3.amazonaws.com/esf-resources/certificates.ks
# that will replace /opt/eurotech/esf/user/security/.certificates.ks
keytool -import -alias ${cert_alias} -keystore certificates.ks -file ${cert_file}Update the ESF Security Policy
After adding the bundle signing certificate(s) to ESF, the security policy file has to be updated accordingly to allow the execution of genuine bundles.
Continuing the example, the new rule to be applied is the following:
<esf:policy>
<esf:access>ALLOW</esf:access>
<esf:conditions>
<esf:condition>
<esf:name>
BundleSignerCondition
</esf:name>
<esf:value>
${dn.name}
</esf:value>
</esf:condition>
</esf:conditions>
<esf:permissions>
<esf:permission>
<esf:name>java.security.AllPermission</esf:name>
<esf:values>
<esf:value>
*
</esf:value>
<esf:value>
*
</esf:value>
</esf:values>
</esf:permission>
</esf:permissions>
<esf:name>
All permissions to bundles signed with this certificate
</esf:name>
</esf:policy>As throughout the example, in the above XML snippet the placeholder ${dn_name} must be replaced with the actual Distinguished Name, for example "CN=www.companyname.com,O=Company Name,C=US".
JAR Signing
Bundles can be signed in the following ways:
-
Using the command line
-
Using Eclipse
-
Using Maven during the build process
Command Line Signature
To sign bundles from the command line, use the jarsigner command:
jarsigner -keystore file:${keystore_file} -tsa http://timestamp.digicert.com \
-storepass ${keystore_pass} -keypass ${key_pass} ${bundle_jar} ${cert_alias}Bundle signature with Eclipse IDE
The Eclipse IDE provides a bundle signing signature feature, abstracting jarsigner.
A simple guide on how to export bundle plugins and how to sign them is available here.
Bundle Verification
In order to verify that the signing has been done correctly in the previous steps, the user can use the jarsigner tool provided by the JVM installation as explained in this page.
Eurotech Certificates
Following the list of all the Eurotech certificates related to bundle signature verification. The certificates are available in PEM format.
For convenience, Eurotech provides a jks keystore containing such certificates. It can be directly used with jarsigner to verify the signature of ESF bundles.
| Resource | Description | Link | MD5 | Status |
|---|---|---|---|---|
| Eurotech Root CA | PEM file containing the Eurotech Root CA | https://esf-website-resources.s3.amazonaws.com/7.2.0/rootCA.pem | d8a156edf9ecae0aa9dadb6de5edbe71 | Active |
| Eurotech Root Software CA | PEM file containing the Eurotech Root Software Intermediate CA | https://esf-website-resources.s3.amazonaws.com/7.2.0/rootSoftwareCA.pem | 58cf2bfb205ae4ff7ec7bf389cb86131 | Active |
| Eurotech Root Software CA 2025 | PEM file containing the Eurotech Root Software Intermediate CA | https://esf-website-resources.s3.us-east-1.amazonaws.com/7.6.0/rootSoftwareCA-20250519.pem | 9b73ab15faaa5303d949ff89406290be | Active |
| Eurotech Root Software ESF CA | PEM file containing the Eurotech Root Software ESF Intermediate CA | https://esf-website-resources.s3.amazonaws.com/7.2.0/rootSoftwareESFCA.pem | c514a2a79dba0a1c493b9e7f40216f68 | Active |
| Eurotech Root Software ESF CA 2025 | PEM file containing the Eurotech Root Software ESF Intermediate CA | https://esf-website-resources.s3.us-east-1.amazonaws.com/7.6.0/rootSoftwareESFCA-20250519.pem | 570e794c48980962c06e6036f530163d | Active |
| EUROTECH S.p.A. ESF Target Platform Signing 2025 | PEM file containing the ESF leaf certificate. Used to sign the ESF target-platform | https://esf-website-resources.s3.us-east-1.amazonaws.com/7.6.0/leafESFTargetPlatformSigning-20250519.pem | 6de855170fc3219bb10a4a87d9950296 | Active. Used to sign since May 2025 |
| EUROTECH S.p.A. ESF Software Signing 2025 | PEM file containing the ESF leaf certificate. Used to sign the ESF core application bundles. | https://esf-website-resources.s3.us-east-1.amazonaws.com/7.6.0/leafESFSoftwareSigning-20250519.pem | adbe5a234d0f8f5d7bebbf9ca6ad6a14 | Active. Used to sign since May 2025 |
| EUROTECH S.p.A. ESF Add-On Bundle Signing 2025 | PEM file containing the ESF add-ons leaf certificate. Used to sign the ESF additional application bundles. | https://esf-website-resources.s3.us-east-1.amazonaws.com/7.6.0/leafESFAddOnSigning-20250519.pem | 2c277e06994e5f14f32b903e6d37685c | Active. Used to sign since May 2025 |
| EUROTECH S.p.A. ESF Target Platform Signing 2024 | PEM file containing the ESF leaf certificate. Used to sign the ESF target-platform | https://esf-website-resources.s3.amazonaws.com/7.5.0/leafESFTargetPlatformSigning-20240503.pem | b5fc560898e9963f1aa71b80352fe338 | Active. Not used to sign since May 2025 |
| EUROTECH S.p.A. ESF Software Signing 2024 | PEM file containing the ESF leaf certificate. Used to sign the ESF core application bundles. | https://esf-website-resources.s3.amazonaws.com/7.5.0/leafESFSoftwareSigning-20240503.pem | af731d465c4dc73905fa402940933529 | Active. Not used to sign since May 2025 |
| EUROTECH S.p.A. ESF Add-On Bundle Signing 2024 | PEM file containing the ESF add-ons leaf certificate. Used to sign the ESF additional application bundles. | https://esf-website-resources.s3.amazonaws.com/7.5.0/leafESFAddOnSigning-20240503.pem | f9bccd1225c8dc5d11dc59f96cd09b33 | Active. Not used to sign since May 2025 |
| EUROTECH S.p.A. ESF Target Platform Signing 2022 | PEM file containing the ESF leaf certificate. Used to sign the ESF target-platform | https://esf-website-resources.s3.amazonaws.com/7.2.0/leafESFTargetPlatformSigning-20220328.pem | a3e0655361382d2aa6aafb44df440591 | Active. Not used to sign since May 2024 |
| EUROTECH S.p.A. ESF Software Signing 2022 | PEM file containing the ESF leaf certificate. Used to sign the ESF core application bundles. | https://esf-website-resources.s3.amazonaws.com/7.2.0/leafESFSoftwareSigning-20220328.pem | c9a13ba5840e3f96768f192c4f35C889 | Active. Not used to sign since May 2024 |
| EUROTECH S.p.A. ESF Add-On Bundle Signing 2022 | PEM file containing the ESF add-ons leaf certificate. Used to sign the ESF additional application bundles. | https://esf-website-resources.s3.amazonaws.com/7.2.0/leafESFAddOnSigning-20220328.pem | d2f7452a5d7f28fc207f5f58ca56eb29 | Active. Not used to sign since May 2024 |
| EUROTECH S.p.A. ESF Target Platform Signing | PEM file containing the ESF leaf certificate. Used to sign the ESF target-platform | https://esf-website-resources.s3.amazonaws.com/7.2.0/leafESFTargetPlatformSigning-20200514.pem | a1fca066525629a9d57ddf84b49b40da | Revoked |
| EUROTECH S.p.A. ESF Software Signing | PEM file containing the ESF leaf certificate. Used to sign the ESF core application bundles. | https://esf-website-resources.s3.amazonaws.com/7.2.0/leafESFSoftwareSigning-20200511.pem | bace0e55a8d50a32e346464712828eb5 | Revoked |
| EUROTECH S.p.A. ESF Add-On Bundle Signing | PEM file containing the ESF add-ons leaf certificate. Used to sign the ESF additional application bundles. | https://esf-website-resources.s3.amazonaws.com/7.2.0/leafESFAddOnSigning-20200611.pem | ea5ef165b2ad5596518b36c589d87c7a | Revoked |
| EUROTECH S.p.A. ESF Customer Bundle Signing CA | PEM file containing the ESF customer CA. | https://esf-website-resources.s3.amazonaws.com/7.2.0/rootSoftwareCustomerCA.pem | 37d7f78097561000aea1cf03404e0daa | Revoked |
| Eurotech Software ESF 1 (old) | PEM file containing the ESF leaf certificate. Used to sign the ESF core application bundles. | https://esf-website-resources.s3.amazonaws.com/7.2.0/softwareESF1.pem | a5017e18d19f20c9e05d0262117d7f28 | Revoked |
| Eurotech Software ESF 2 (old) | PEM file containing the ESF leaf certificate. Used to sign the ESF target-platform | https://esf-website-resources.s3.amazonaws.com/7.2.0/softwareESF2.pem | 2f01ecfdc9a7b38bb86661c6e8e8eb39 | Revoked |
| Eurotech Trust Store | JKS file containing all the CAs and that can be directly used to check the bundle signature | https://esf-website-resources.s3.amazonaws.com/7.2.0/certificates.ks | 7b0131d48aa64ecb2a89e487db66f02f |
Updated 4 months ago
