Network Threat Manager
ESF provides a set of features to detect and prevent network attacks. The Network Threat Manager tab in the Security section of the Gateway Administration Console allows the user to activate these functions.
The Network Threat Manager tab is not available for the No Network version of ESF.
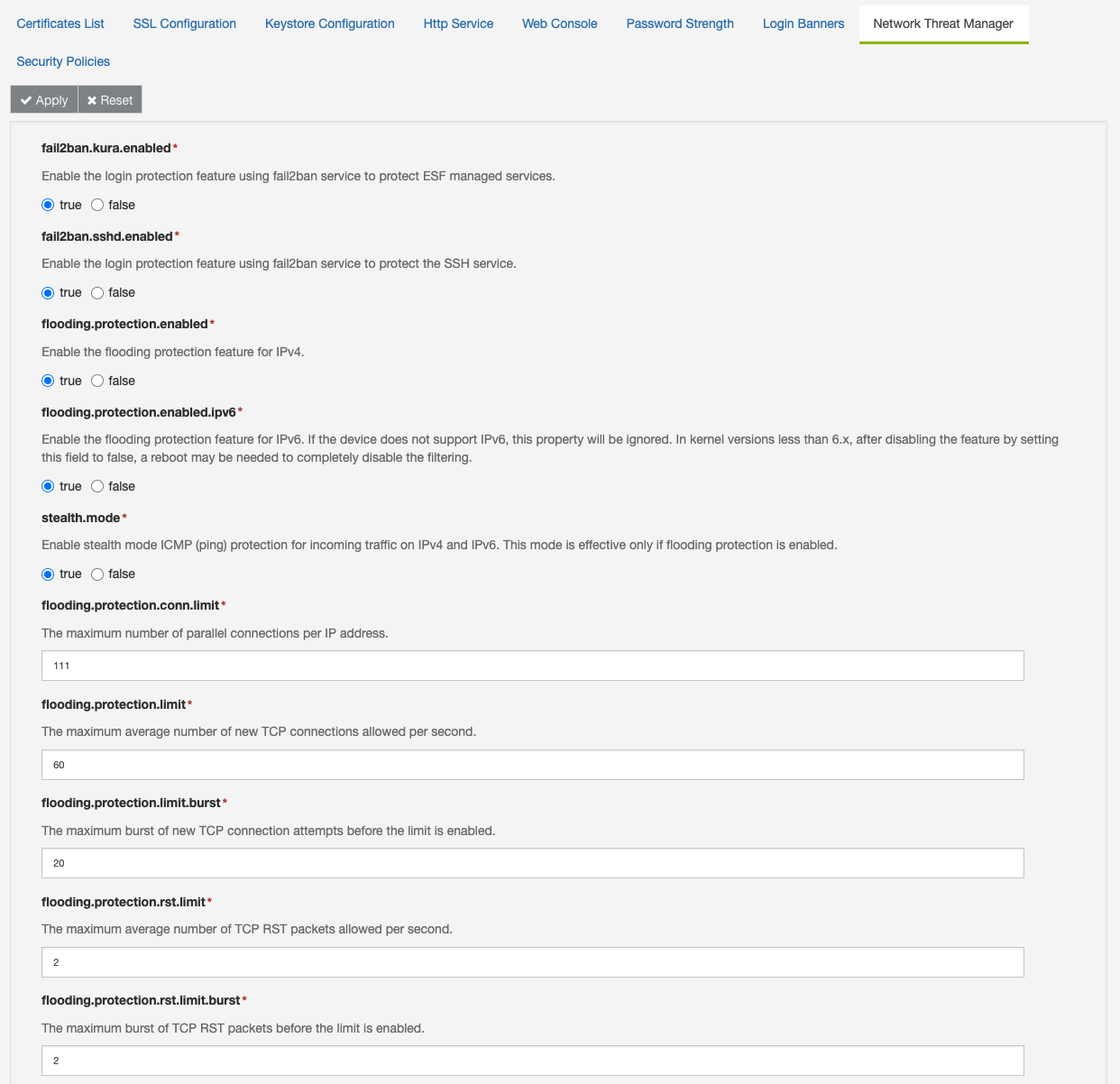
The following functions are supported:
- Flooding protection (for both IPv4 and IPv6)
- Fail2Ban
Flooding protection
The flooding protection function is used to prevent DDos (Distributed Denial-of-Service) attacks using specific firewall rules. When enabled, the feature modifies the filter and mangle tables in the iptables and ip6tables firewall to prevent or limit common attacks.
The following parameters are available:
- flooding.protection.enabled : enables the application of the IPv4 firewall rules for flooding protection;
- flooding.protection.enabled.ipv6 : enables the application of the IPv6 firewall rules for flooding protection on devices that support it; if a device does not support IPv6, the property has not effect.
- stealth.mode : Enable stealth mode ICMP (ping) protection for incoming traffic on both IPv4 and IPv6. This mode is effective only when flooding protection is activated. When stealth mode is enabled, all incoming ping requests are blocked. Outgoing ping replies are rate-limited according to the thresholds specified by flooding.protection.icmp.limit and flooding.protection.icmp.limit.burst. If stealth.mode is disabled, incoming ping requests are permitted, but both incoming and outgoing pings are rate-limited based on the limits defined above.
- flooding.protection.conn.limit : sets the maximum number of parallel connections per IP address; it corresponds to the KURA_CONN_LIMIT parameter.
- flooding.protection.limit : sets the maximum average number of new TCP connections allowed per second; it corresponds to the KURA_LIMIT parameter.
- flooding.protection.limit.burst : sets the maximum burst of new TCP connection attempts before the limit is enabled; it corresponds to the KURA_BURST_LIMIT parameter.
- flooding.protection.rst.limit : sets the maximum average number of TCP RST packets allowed per second; it corresponds to the KURA_RST_LIMIT parameter.
- flooding.protection.rst.limit.burst : sets the maximum burst of TCP RST packets before the RST limit is triggered; it corresponds to the KURA_RST_BURST_LIMIT parameter.
- flooding.protection.icmp.limit : sets the maximum average number of ICMP packets allowed per second; it corresponds to the KURA_ICMP_LIMIT parameter.
- flooding.protection.icmp.limit.burst : sets the maximum burst of ICMP packets before the limit is triggered; it corresponds to the KURA_ICMP_BURST_LIMIT parameter.
Flooding protection for IPv4
When the feature is enabled with the flooding.protection.enabled and stealth.mode properties, the following rules are added to the mangle table and they are implemented to block invalid or malicious network packets:
-A prerouting-kura -m conntrack --ctstate INVALID -j DROP
-A prerouting-kura -p tcp -m tcp ! --tcp-flags FIN,SYN,RST,ACK SYN -m conntrack --ctstate NEW -j DROP
-A prerouting-kura -p tcp -m conntrack --ctstate NEW -m tcpmss ! --mss 536:65535 -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN FIN,SYN -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags SYN,RST SYN,RST -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,RST FIN,RST -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,ACK FIN -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags ACK,URG URG -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,ACK FIN -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags PSH,ACK PSH -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,PSH,ACK,URG -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG NONE -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,PSH,URG -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,PSH,URG -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,ACK,URG -j DROP
-A prerouting-kura -p icmp -m icmp --icmp-type 8 -m state --state NEW,RELATED,ESTABLISHED -j DROP
-A prerouting-kura -p icmp -m icmp --icmp-type 0 -m state --state NEW,RELATED,ESTABLISHED -m limit --limit KURA_ICMP_LIMIT/sec --limit-burst KURA_ICMP_BURST_LIMIT -j ACCEPT
-A prerouting-kura -p icmp -m icmp --icmp-type 0 -j DROP
-A prerouting-kura -f -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags RST RST -m limit --limit KURA_RST_LIMIT/sec --limit-burst KURA_RST_BURST_LIMIT -j ACCEPT
-A prerouting-kura -p tcp -m tcp --tcp-flags RST RST -j DROP
-A prerouting-kura -p tcp -m conntrack --ctstate NEW -m limit --limit KURA_LIMIT/sec --limit-burst KURA_BURST_LIMIT -j ACCEPT
-A prerouting-kura -p tcp -m conntrack --ctstate NEW -j DROPThe following rules, instead, are added to the filter table and they are intended to limit the number of incoming TCP connections:
-A input-kura -p tcp -m connlimit --connlimit-above KURA_CONN_LIMIT --connlimit-mask 32 --connlimit-saddr -j REJECT --reject-with tcp-resetTo further filter the incoming TCP fragmented packets, the values in ipfrag_low_thresh and ipfrag_high_thresh
are set to 0.
Flooding Protection for IPv6
When the feature is enabled with the flooding.protection.enabled and stealth.mode properties, the following rules are applied to the mangle table:
-A prerouting-kura -m conntrack --ctstate INVALID -j DROP
-A prerouting-kura -p tcp -m tcp ! --tcp-flags FIN,SYN,RST,ACK SYN -m conntrack --ctstate NEW -j DROP
-A prerouting-kura -p tcp -m conntrack --ctstate NEW -m tcpmss ! --mss 536:65535 -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN FIN,SYN -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags SYN,RST SYN,RST -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,RST FIN,RST -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,ACK FIN -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags ACK,URG URG -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,ACK FIN -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags PSH,ACK PSH -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,PSH,ACK,URG -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG NONE -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,PSH,URG -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,PSH,URG -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags FIN,SYN,RST,PSH,ACK,URG FIN,SYN,RST,ACK,URG -j DROP
-A prerouting-kura -p ipv6-icmp -m icmp6 --icmpv6-type 128 -j DROP
-A prerouting-kura -m ipv6header --header ipv6-opts --soft -j DROP
-A prerouting-kura -m ipv6header --header hop-by-hop --soft -j DROP
-A prerouting-kura -m ipv6header --header ipv6-route --soft -j DROP
-A prerouting-kura -m ipv6header --header ipv6-frag --soft -j DROP
-A prerouting-kura -m ipv6header --header ah --soft -j DROP
-A prerouting-kura -m ipv6header --header esp --soft -j DROP
-A prerouting-kura -m ipv6header --header ipv6-nonxt --soft -j DROP
-A prerouting-kura -p tcp -m tcp --tcp-flags RST RST -m limit --limit KURA_RST_LIMIT/sec --limit-burst KURA_RST_BURST_LIMIT -j ACCEPT
-A prerouting-kura -p tcp -m tcp --tcp-flags RST RST -j DROP
-A prerouting-kura -p tcp -m conntrack --ctstate NEW -m limit --limit KURA_LIMIT/sec --limit-burst KURA_BURST_LIMIT -j ACCEPT
-A prerouting-kura -p tcp -m conntrack --ctstate NEW -j DROP
-A prerouting-kura -p ipv6-icmp -m limit --limit KURA_ICMP_LIMIT/sec --limit-burst KURA_ICMP_BURST_LIMIT -j ACCEPT
-A prerouting-kura -p ipv6-icmp -j DROPThe rules applied to the filter table are the same of the IPv4 case and the configured parameters are applied to both cases.
To further filter the incoming TCP fragmented packets, the values in nf_conntrack_frag6_low_thresh and nf_conntrack_frag6_high_thresh are set to 0.
To recover the device state when the IPv6 flooding protection feature is disabled, a reboot is required. So, to disable the feature, set the flooding.protection.enabled.ipv6 property to false and reboot the device.
Fail2Ban
Fail2ban is a tool used for intrusion detection and prevention. It scans system and ESF log files and bans the IP addresses that show some malicious signs (i.e. too many password failures, etc.). Fail2Ban is used to update firewall rules to reject the IP addresses for a specified amount of time.
The Fail2Ban feature can be enable both for ESF and ssh accesses. The fail2ban.kura.enabled parameter enables the monitoring of ESF accesses, while the fail2ban.sshd.enabled one activates the monitoring of accesses via ssh.
Updated 4 months ago
