EST Enrollment Service
The Enrollment over Secure Transport, or EST is a cryptographic protocol that describes an X.509 certificate management protocol targeting public key infrastructure (PKI) clients that need to acquire client certificates and associated certificate authority (CA) certificates.
EST is described in RFC 7030 and uses HTTPS as transport and leverages TLS for many of its security attributes.
The EST Enrollment Service allows the system to generate a Certificate Signing Request (CSR) to be submitted to a Certificate Autorithy (CA) in order to receive a valid Certificate.
The service download the CA certificates storing them in the selected KeystoreService with the alias prefix est-cacerts_.
The generated private KeyPair will be stored in the selected KeystoreService with the alias est-request-key-pair.
The signed certificate received from the EST server will be stored in the KeystoreService with the alias est-enrolled-key-pair.
The service will retry the operation according to the configured parameter Connect Retry-interval, by default every 60 seconds.
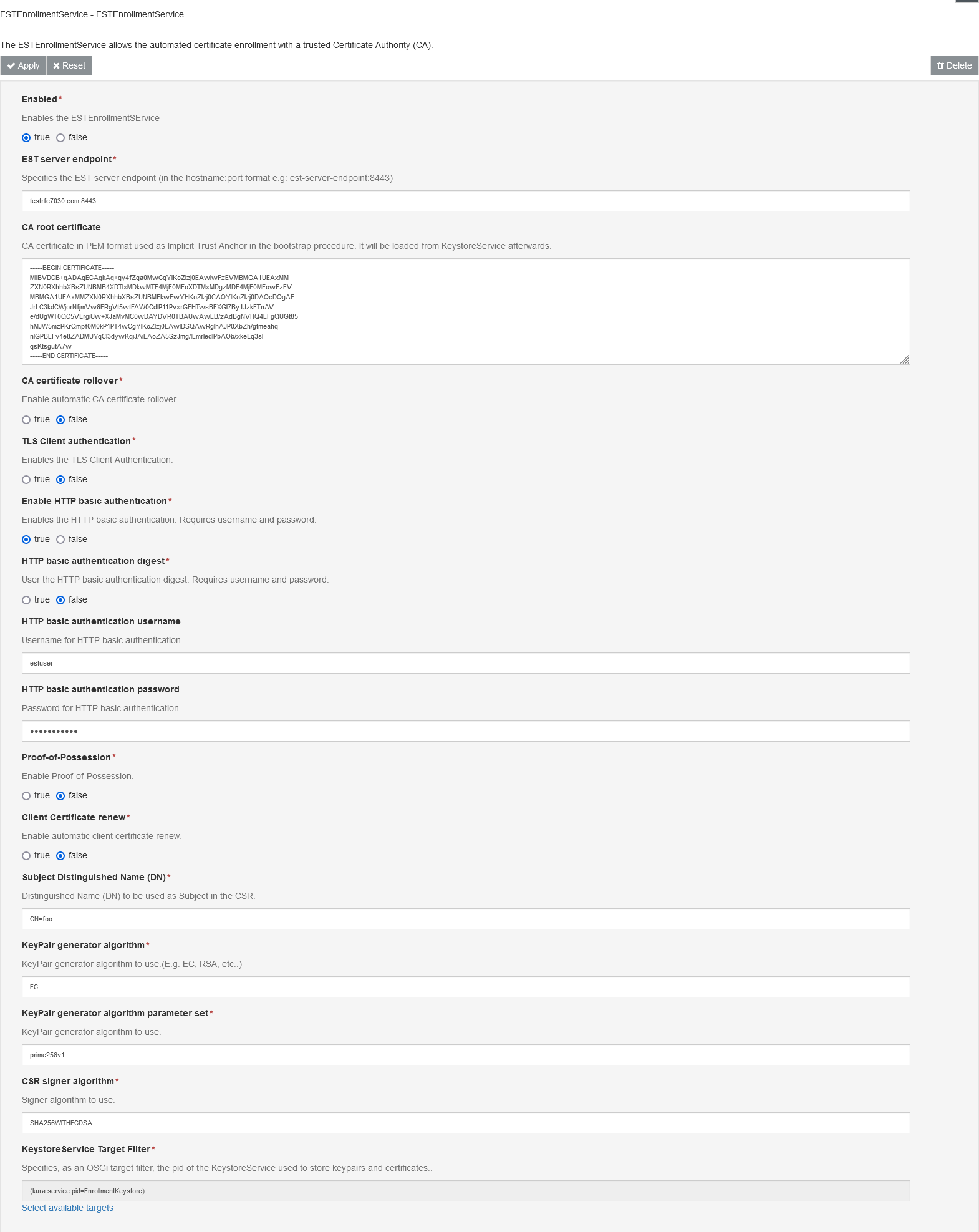
The ESTEnrollmentService component can be configured with the following attributes:
-
KeystoreService Target Filter: Specifies, as an OSGi target filter, the pid of the KeystoreService to be used to store keypairs and certificates.
-
Enabled: Enables the ESTEnrollmentService.
-
EST server endpoint: Specifies the EST server endpoint (in the hostname:port format e.g: est-server-endpoint:8443).[1]
EST server endpoint URLThe protocol (e.g. http or https) must not be included.
-
CA root certificate: Certificate Authority root certificate in PEM format used as Implicit Trust Anchor in the bootstrap procedure. It will be loaded from KeystoreService afterwards.[1]
-
CA certificate rollover: Enables automatic Certificate Authority certificates rollover.
-
Certificate expiration check time: In the case of client certificate a renew attempt will be made . In the case of CA certificates an update attempt will be made according with the protocol.
-
Connect Retry-interval: Specifies the time interval between two attempts in the enrollment process.
-
TLS Client authentication: Enables the TLS Client Authentication. The selected KeystoreService must contains a TLS Client certificate with the alias
client-auth-certs -
Enable HTTP basic authentication: Enables the HTTP basic authentication. Requires an username and password.
-
HTTP basic authentication digest: Use the HTTP basic authentication digest. Requires username and password.
-
HTTP basic authentication username: Username required for HTTP basic authentication.
-
HTTP basic authentication password: Password required HTTP basic authentication.
-
Proof-of-Possession: Enable Proof-of-Possession. Proof-of-Possession allows the client to prove that it has possession of (i.e., is able to use) the private key corresponding to the public key for which a certificate is requested.
-
Client Certificate renew: Enables automatic client certificate renewing.
-
Subject Distinguished Name (DN): Distinguished Name (DN) in X.500 format to be used as Subject in the CSR.
-
KeyPair generator algorithm: KeyPair generator algorithm to use. At the moment the only supported algorith are EC and RSA
-
KeyPair generator algorithm parameter set: KeyPair generator parameter set to use. For RSA this is the size of the key (e.g. 2048 or 4096). For EC this is the name of a standard elliptic curve (e.g. prime256v1).
-
CSR signer algorithm: Signer algorithm to use to sign the Certificate Signing Request. Tipically they are SHA256WITHECDSA for EC and SHA256WITHRSA for RSA.
[1] A change in this property triggers a new client bootstrap with a subsequent enrollment
Updated 4 months ago
