Startup Security Checks
In production mode, ESF performs the following security checks on startup:
ESF will shut down if anyone of these checks fail.
Policy File Fingerprint
The policy file fingerprint is taken and stored in a protected area, the first time that ESF starts in production mode.
At every successive boot, ESF recalculates the policy file fingerprint and compares it with the one stored in its protected storage area.
In production mode, the fingerprint protected by ESF needs to be refreshed for every change in the security policy file.
Edit ESF Security Policy File and Reload the Corresponding Fingerprint
1.With ESF running edit /opt/eurotech/esf/user/security/security.policy
2. Log into the ESF Gateway Administration Console
3. Navigate to System | Settings. In the Security Policies tab click the Reload fingerprint button of Security Policy.
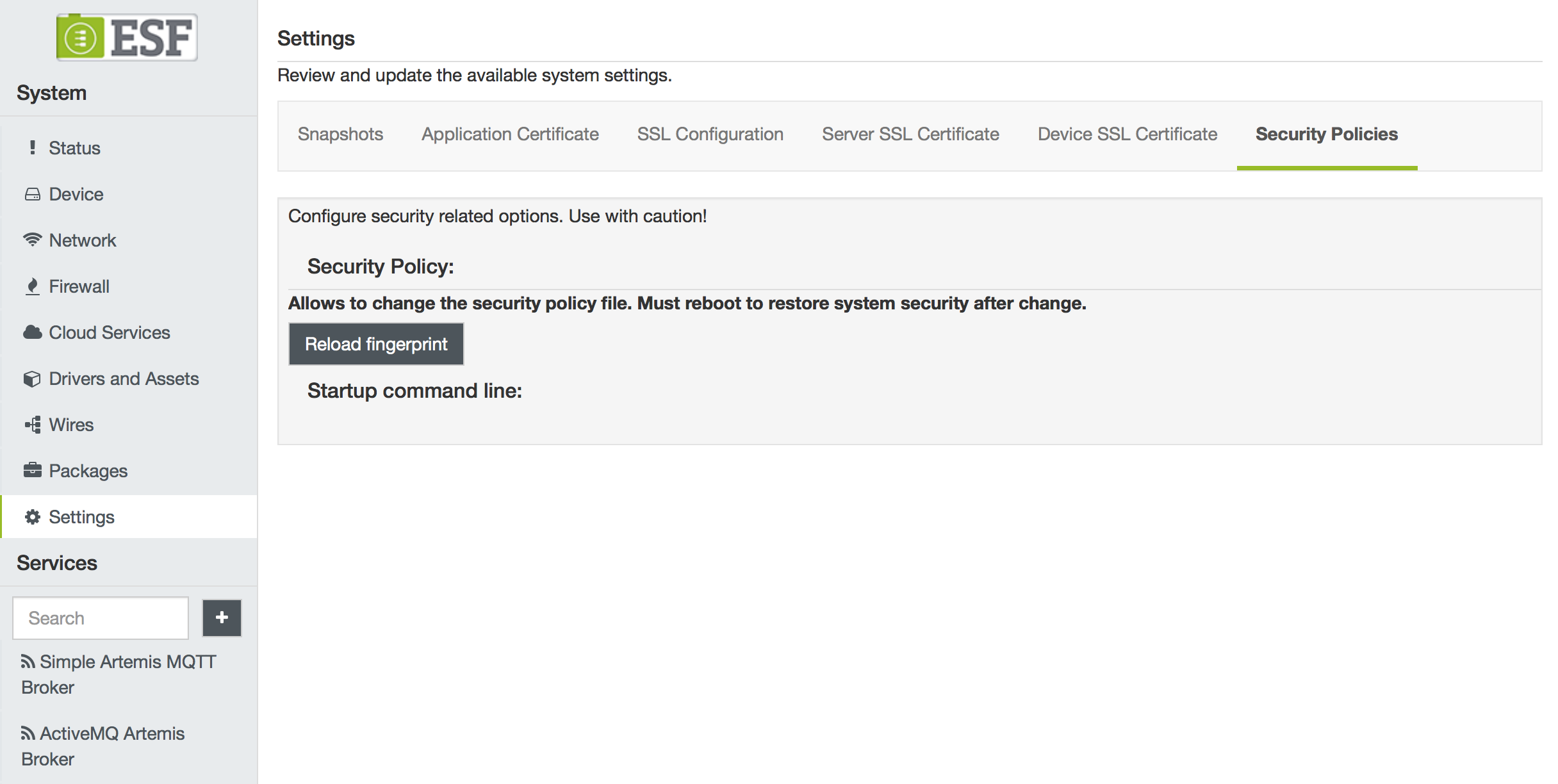
The switch between framework execution modalities (from development to production mode or from production mode to development mode) requires the reload of both the Security Policy and Startup Command Line fingerprints.
ESF launch script fingerprint
Like for the security policy file, the command line script used to run the ESF Java process is fingerprinted at ESF first boot in production mode and verified at every startup.
The command line script can be found at the following path: /opt/eurotech/esf/bin/start_kura_background.sh.
In production mode, if the ESF launch script needs to be changed, the user must require ESF to reload the corresponding fingerprint.
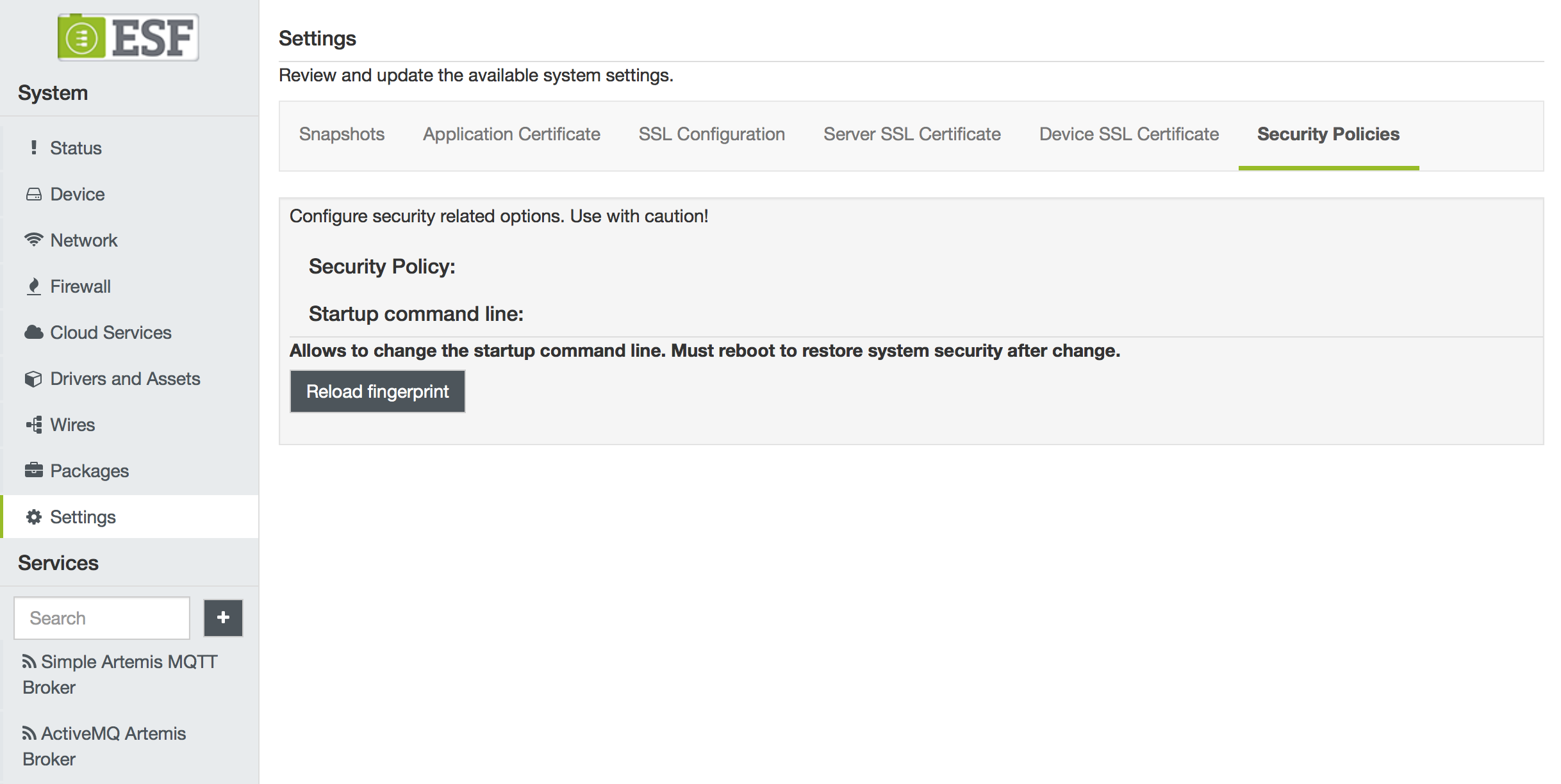
Edit ESF Launch Script File and Reload the Corresponding Fingerprint
1.With ESF running, edit /opt/eurotech/esf/bin/start_kura_background.sh
2. Log into the ESF Gateway Administration Console
3. Navigate to System | Settings. In the Security Policies tab click the Reload fingerprint button of Startup command line.
Java Virtual Machine Options
In production mode, ESF checks various JVM options to protect against the use of profilers and debuggers that could disclose confidential information.
-
HeapDumpPath - is set to /dev/null
-
-Xdebug - is not defined
-
-Xrunjdwp - is not defined
-
-Xbootclasspath: - is not defined
-
-XX:StartFlightRecording - is not defined
-
-agentlib: - is not defined
-
-agentpath: - is not defined
-
-verbose - is not defined
Updated 4 months ago
