H2Db Service
ESF integrates a Java SQL database named H2. The main features of this SQL Database are:
- Very fast, open source, JDBC API
- Embedded and server modes; in-memory databases
- Browser-based Console application
- Small footprint
Supported Features
ESF supports the following H2 database features:
-
Persistence modes: The H2 implementation currently supports in-memory and file-based database instances. See the Persistence Modes section for more details.
-
Multiple database instances: It is possible to create and configure multiple database instances from the ESF Administration UI, these instances can be selectively consumed by applications. A default database instance is created automatically.
-
TCP Server: The current implementation allows external processes to access the database instances managed by ESF using TCP. This enables the integration of external applications that can share data with ESF components using the database.
-
Web-based console: It is possible to start the H2 Web console directly from the ESF Administration UI. The console can be used to inspect the database contents and perform arbitrary queries for debug purposes.
-
Basic credential management: The current implementation allows to change the password of the admin DB user from the ESF Administration UI. This allows the access restriction to the existing database instances.
By default, the DataService in ESF uses the H2 database to persist the messages.
Limitations
-
Private in-memory instances: Only named in-memory instances are supported (e.g.
jdbc:h2:mem:<dbname>, where<dbname>is not the empty string), private instances represented by thejdbc:h2:mem:URL are currently not supported. -
Remote connections: The current implementation only supports embedded database instances. Connecting to remote instances using the
jdbc:h2:tcp:*andjdbc:h2:ssl:*connector URLs is not supported.
Usage
Creating a new H2 database instance
To create a new H2 database instance, use the following procedure:
- Open the ESF Administrative UI and press the + button in the side menu, under the Services section. A pop-up dialog should appear.
- Select
org.eclipse.kura.core.db.H2DbServicefrom the Factory drop-down list, enter an arbitrary name for the new instance and click Apply.
- An entry for the newly created instance should appear in the side menu under Services, click on it to review its configuration:
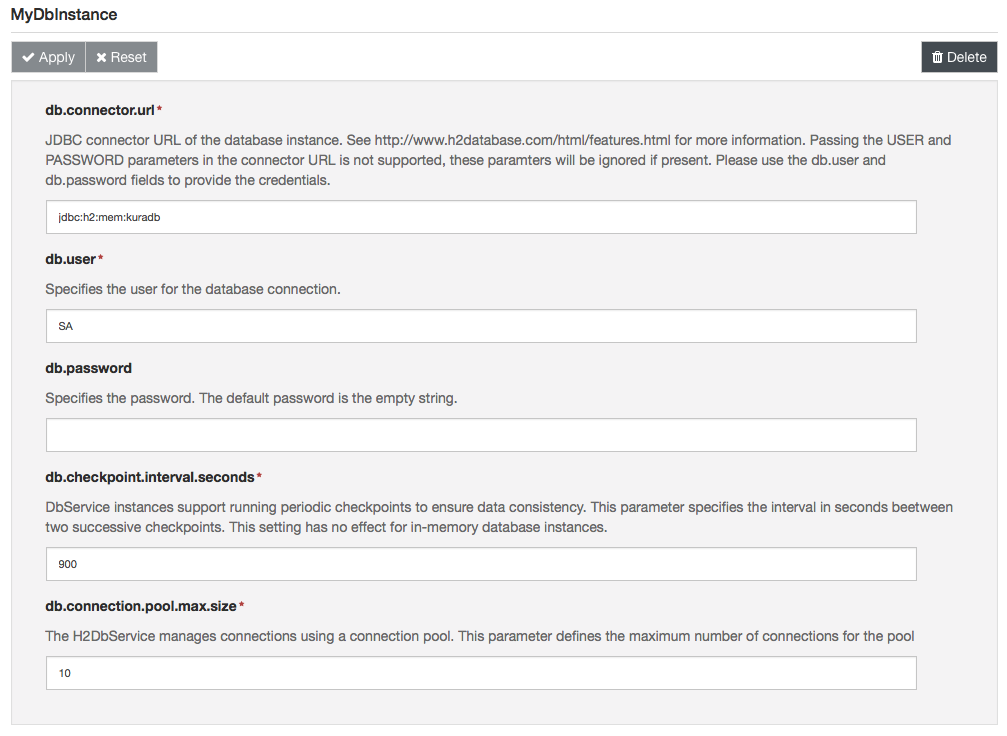
Configuration Parameters
The H2DbService provides the following configuration parameters:
- Connector URL: JDBC connector URL of the database instance. Passing the USER and PASSWORD parameters in the connector URL is not supported, these paramters will be ignored if present. Please use the db.user and db.password fields to provide the credentials.
WarningIf the database is created in persisted mode, please make sure that the Linux user running ESF (
esfd) has the permissions required to create the database file.
If the permissions are not ok, ESF may be able to create the database (by default it runs with the CAP_DAC_OVERRIDE capability) but it may not be able to perform the periodic defragmentation process, this may cause the database file size to grow especially if the write rate is high.Executing the following commands as
rootcan be useful to detect potential issues, replacedatabase_parent_directorywith the parent directory of the database file.export TARGET="$(readlink -f database_parent_directory)" sudo -u esfd sh -c "touch '${TARGET}/.testfile' && rm '${TARGET}/.testfile'"If command fails it may be necessary to change the database directory or adjust the permissions.
-
User: Specifies the user for the database connection. Furthermore
-
Password: Specifies the password. The default password is the empty string.
-
Checkpoint interval (seconds): H2DbService instances support running periodic checkpoints to ensure data consistency. This parameter specifies the interval in seconds between two successive checkpoints. This setting has no effect for in-memory database instances.
-
Defrag interval (minutes): H2DbService instances support running periodic defragmentation (compaction). This parameter specifies the interval in minutes between two successive checkpoints, set to zero to disable. This setting has no effect for in-memory database instances. Existing database connections will be closed during the defragmentation process and need to be reopened by the applications.
-
Connection pool max size: The H2DbService manages connections using a connection pool. This parameter defines the maximum number of connections for the pool
It is not possible to create different DB instances that manage the same DB URL. When creating a new instance please make sure that the URL specified in the field db.connector.url is not managed by another instance.
Selecting a Database Instance for Existing ESF Components
A database instance is identified by its Kura service PID. The PID for the default instance is org.eclipse.kura.db.H2DbService while the PID for instances created using the Web UI is the string entered in the Name field at step 2 of the previous section.
The built-in ESF components that use database functionalities allow to specify which instance to use in their configuration. These components are the DataService component of the cloud stack, the H2DbWireRecordFilter and H2DbWireRecordStore wire components.
The configuration of each component contains a property that allows to specify the service PID of the desired instance.
Enabling the TCP Server
Development-only featureThis feature is intended to be used only for debugging/development purposes. The server created by H2 is not running on a secure protocol. Only enable the server for a limited time and make sure to properly secure the firewall ports on which it is running.
The TCP server can be used by creating a H2DbServer instance:
- Open the ESF Web UI and press the + button in the side menu, under the Services section. A pop-up dialog should appear.
- Select
org.eclipse.kura.core.db.H2DbServerfrom the Factory drop-down list, enter an arbitrary name for the new instance and click Apply.
- Clicking on the name of the new server instance on the left side of the Web UI. The configuration of the server component will appear:
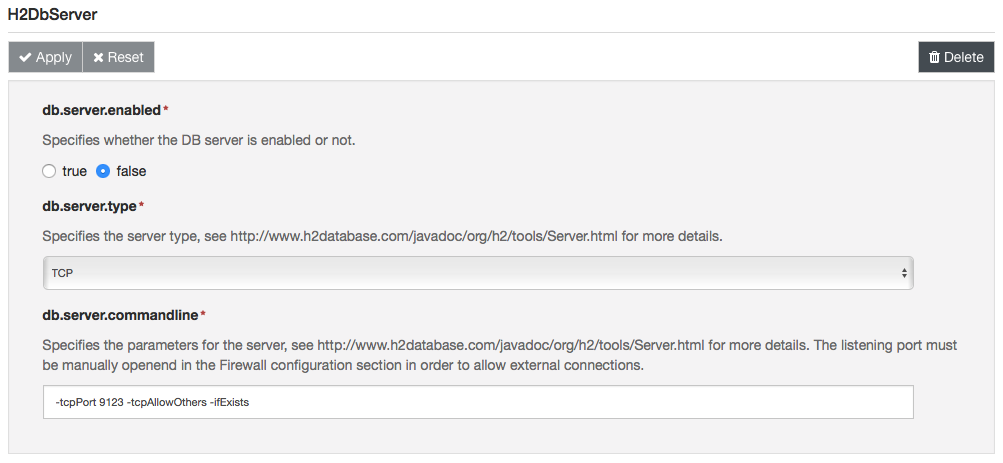
- Set the db.server.type field to TCP
- Review the server options under db.server.commandline, check the official documentation for more information about the available options.
- Set the db.server.enabled to true.
The server, with the default configuration, will be listening on port 9123.
Make sure to review the firewall configuration in order to ensure that the server is reachable from an external process.
Enabling the Web Console
Development-only featureThis feature is intended to be used only for debugging/development purposes. The server created by H2 is not running on a secure protocol. Only enable the server for a limited time and make sure to properly secure the firewall ports on which it is running.
In order to enable the H2 Web console, proceed as follows:
- Create a new H2DbServer instance.
- Set the db.server.type field to WEB
- Enter appropriate parameters for the Web server in the db.server.commandline field. An example of valid settings can be -webPort 9123 -webAllowOthers -ifExists.
- Set the db.server.enabled to true.
The server is now listening on the specified port.
Make sure to review the firewall configuration in order to ensure that the server is reachable from an external process.
Use a browser to access the console. Open the http://<device-ip>:<web-console-port> URL, where <device-ip> is the IP address of the ESF device and <web-console-port> is the port specified at step 3.
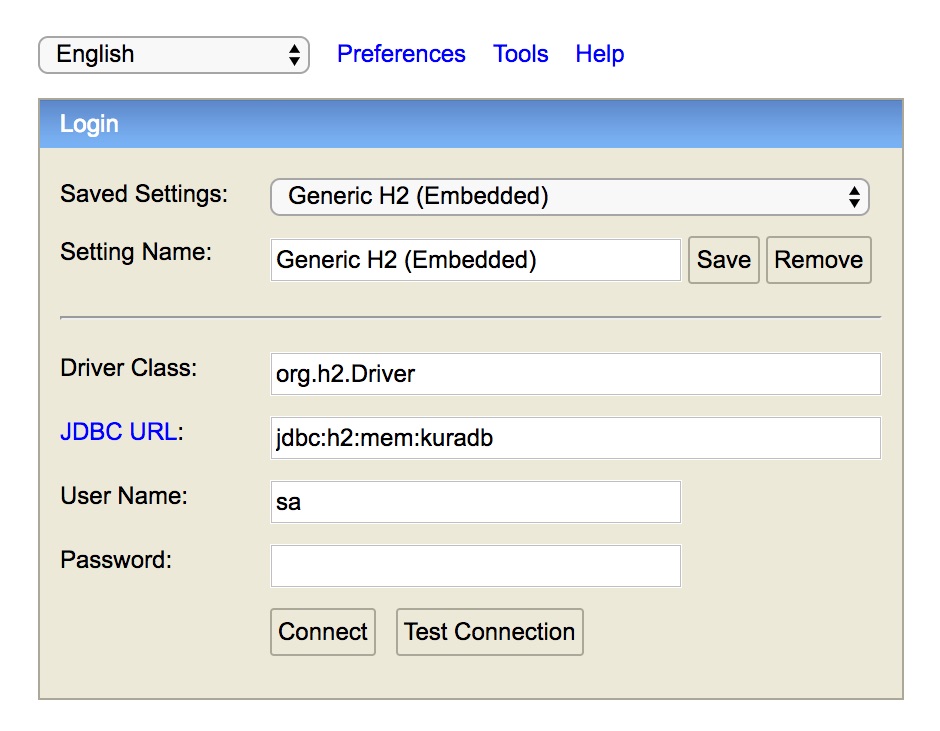
Enter the DB URL as specified in the Kura configuration in the JDBC URL field and the credentials. Click on Connect, you should be able to access the console.
Change the Database Password
To change the database password the System Administrator needs to:
- Open the configuration of the desired database instance in the ESF Web UI.
- Enter the new password in the db.password field.
- Click Apply.
If the H2DbServer instance fails to open a database, it will delete and recreate all database files. This behavior is aimed at preventing potential issues caused by incorrect credentials in the configuration snapshots. It is highly recommended to perform a backup of an existing database before trying to open it using a H2DbService instance and before changing the password.
Persistence Modes
The H2 database supports several persistence modes.
In Memory
An in-memory database instance can be created using the following URL structure: jdbc:h2:mem:<dbname>, where <dbname> is a non-empty string that represents the database name. This configuration is suggested for database instances that are frequently updated. Examples:
- jdbc:h2:mem:kuradb
- jdbc:h2:mem:mydb
The default database instance is in-memory by default and uses the jdbc:h2:mem:kuradb URL.
Most Persistent
A persistent database instance can be created using the jdbc:h2:file:<dbpath>, where <dbpath> is a non-empty string that represents the database path.
If no URL parameters are supplied the database will enable the transaction log by default. The transaction log is used to restore the database to a consistent state after a crash or power failure. This provides good protection against data losses but causes a lot of writes to the storage device, reducing both performance and the lifetime of flash-based storage devices.
This configuration is suggested for database instances that are rarely updated. Examples:
- jdbc:h2:file:/opt/db/mydb
Make sure to use absolute paths in the DB URL since H2 does not support DB paths relative to the working directory.
ESF versions with the embedded H2DB (version < 1.4.199) can be affected by database corruption when the database is persisted in the filesystem.Eurotech suggests the update to ESF 6.1.2 that provides H2DB v.1.4.199.
The database format used by H2DB v.1.4.199 is incompatible with the one used in previous versions of the product. In case of an upgrade of an ESF instance with a persisted database to 6.1.2, the customer has to delete/upgrade the existing persisted database to be compatible with this new version. Please refer to http://www.h2database.com/html/tutorial.html#upgrade_backup_restore
Mostly Persistent
The transaction log can be disabled by appending the LOG=0 parameter to the DB URL. In this way, it is possible to reduce the stress on the underlying storage device and increase performance, at the expense of a higher probability of losing data in case of power failure.
In order to reduce the probability of data losses, the H2DbService performs periodic checkpoints on the database. A checkpoint forces all pending modifications to be committed to the storage device. The interval in seconds between two consecutive checkpoints can be configured using the db.checkpoint.interval.seconds property.
This configuration is suggested for database instances with intermediate update rates. Examples:
- jdbc:h2:file:/opt/db/mydb;LOG=0
ESF versions with the embedded H2DB (version < 1.4.199) can be affected by database corruption when the database is persisted in the filesystem.Eurotech suggests the update to ESF 6.1.2 that provides H2DB v.1.4.199.
The database format used by H2DB v.1.4.199 is incompatible with the one used in previous versions of the product. In case of an upgrade of an ESF instance with a persisted database to 6.1.2, the customer has to delete/upgrade the existing persisted database to be compatible with this new version. Please refer to http://www.h2database.com/html/tutorial.html#upgrade_backup_restore
Filesystem Tuning
The H2 file-backed database might become corrupted in case of power failure.
The following mount options can improve database reliability, reducing the database corruption probability at the expense of reduced performance and lifetime of the storage device:
-
data=journal: From EXT4(5) Linux MAN Page:All data is committed into the journal prior to being written into the main filesystem.
-
sync: From mount(8) Linux MAN Page:All I/O to the filesystem should be done synchronously. In case of media with limited number of write cycles (e.g. some flash drives) "sync" may cause life-cycle shortening.
After some long running tests, it appears that the data=journal option alone is enough to reduce corruption probability (no corruption observed during the test).
The currently recommended mount in /etc/fstab is as follows for the data partition of the ReliaGATE 10-12, if Docker is not installed:
/dev/mmcblk0p7 /mnt/data auto defaults,data=journal,x-systemd.device-timeout=30,x-systemd.mount-timeout=30,nofail 0 2If Docker is installed /etc/fstab the data partition is already mounted as follows:
/dev/mmcblk0p7 /var/lib/docker auto defaults 0 0To use this partition also for the H2 database, the line should be changed to:
/dev/mmcblk0p7 /var/lib/docker auto defaults,data=journal,x-systemd.device-timeout=30,x-systemd.mount-timeout=30,nofail 0 2Please note that the change would be reverted if the Docker package is re-installed or updated.
Alternatively, the configuration partition can be dedicated to the H2 database:
/dev/mmcblk0p5 /mnt/data auto defaults,data=journal,x-systemd.device-timeout=30,x-systemd.mount-timeout=30,nofail 0 2The BoltGATE 20-25 can leverage an SSD (factory option) for the H2 database:
UUID=<partition UUID> /mnt/data auto defaults,data=journal,x-systemd.device-timeout=30,x-systemd.mount-timeout=30,nofail 0 2where the actual <partition UUID> of the SSD can be found executing the command blkid.
In order to reduce disk writes to a minimum noatime can be added to the mount options:
UUID=<partition UUID> /mnt/data auto defaults,data=journal,noatime,x-systemd.device-timeout=30,x-systemd.mount-timeout=30,nofail 0 2Enhance H2 security
The H2 version used in ESF (v.1.4.199) is currently affected by CVE-2021-23463 and CVE-2021-42392. Out of the box, the ESF framework and ESF bundles are not affected by these vulnerabilities. However, custom-made bundles/applications might use some advanced H2 features that could expose the application to the following vulnerabilities:
CVE-2021-23463
This vulnerability allows for a XML External Entity (XXE) Injection via the org.h2.jdbc.JdbcSQLXML class object, when it receives parsed string data from org.h2.jdbc.JdbcResultSet.getSQLXML() method. If it executes the getSource() method when the parameter is DOMSource.class it will trigger the vulnerability.
By default, ESF and Eurotech add-ons do not use or expose such class and methods. A third party application may use such classes and it should be checked to verify that it properly verify the content provided to such class.
CVE-2021-42392
The org.h2.util.JdbcUtils.getConnection method of the H2 database takes as parameters the class name of the driver and URL of the database. An attacker may pass a JNDI driver name and a URL leading to a LDAP or RMI servers, causing remote code execution. This can be exploited through various attack vectors, most notably through the H2 Console which leads to unauthenticated remote code execution.
As stated above, the H2 console is a feature intended for development purposes only and should never be enabled in production mode.
Vulnerabilities mitigation
This mitigation disables the usage of classes that do not belong to packages com.h2 and org.h2. This is quite restrictive, so exceptions can be added, like Java triggers or function aliases, database event listeners, table engines, or JAVA_OBJECT data type.
Modify the /opt/eurotech/esf/bin/start_kura_backgroud.sh file while ESF is up and running by adding the following property:
-Dh2.allowedClasses=com.h2.*,org.h2.* \If in development mode, nothing else has to be done. If in production mode, then reload the fingerprint of the startup command line and reboot (Security -> Security Policies -> click on Startup command line -> Reload fingerprint). If you want to revert the changes because some bug happened or else, then remove the previously added line and reload the startup command line fingerprint while ESF is running.
Updated 4 months ago
