AIDE Intrusion Detection
ESF 7 adds support for monitoring a set of files for changes using the AIDE tool for intrusion detection purposes.
The tool can perform the following actions:
- INIT: Creates a database containing fingerprint information about the monitored files.
- CHECK: Compares the current state of the monitored files with the fingerprints stored in database, reporting any difference.
ESF is able to apply AIDE configuration performing the INIT action and then periodically monitor system state with the CHECK action.
AIDE support is implemented as a Kura TamperDetectionService implementation (see Tamper Detection for more information), the integrity check result is reported as part of the tamper status. Resetting the tamper status causes the INIT action to be performed.
The tamper status reported by the AIDE TamperDetectionService contains the following custom properties:
- AIDE Output: The stdout of the last AIDE invocation, reports information about changed files.
- AIDE Command: Reports whether the last AIDE execution performed the INIT or CHECK action.
The properties above can be missing if the first AIDE execution after device startup has not been performed yet.
AIDE is not available in docker images. It is possible to map the host machine AIDE binary to the docker container allowing ESF to use it for tampering detection.
## Configuration
AIDE integration can be configured in the AIDE Tamper Detection section under Services.
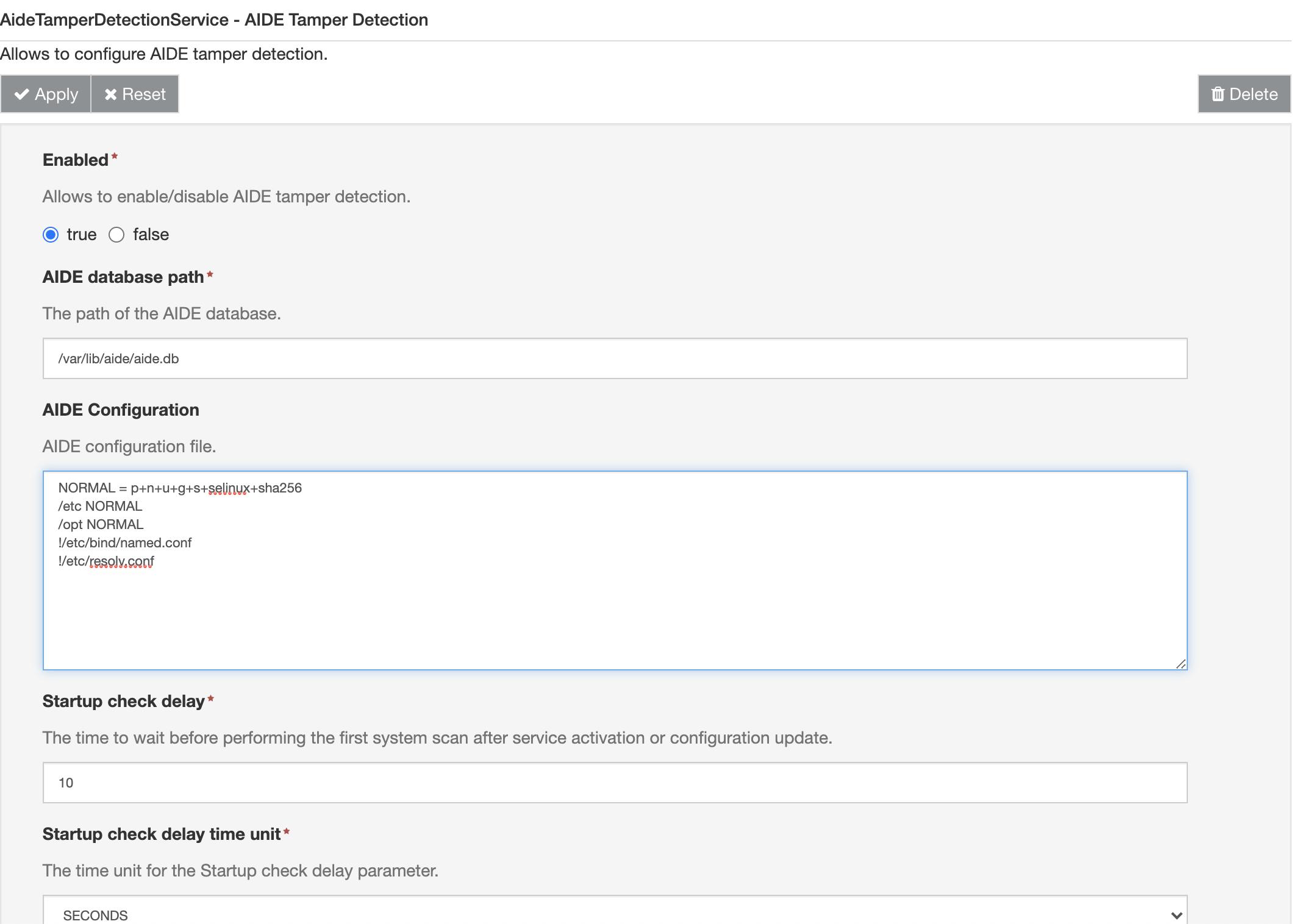
The following parameters are avaliable:
Enabled: Allows to enable/disable AIDE tamper detection integration.
AIDE database path: This parameter allows to configure the database location.
AIDE Configuration: Allows to specify the AIDE configuration, this allows to specify the set of files that should be monitored by the tool. Please refer to the aide.conf Linux man page for more details.
An example configuration file is the following:
NORMAL = p+n+u+g+s+selinux+sha256
/etc NORMAL
/opt NORMAL
!/etc/bind/named.conf
!/etc/resolv.conf
!/etc/adjtime*This configuration contains the following directives:
- All files under
/etcand/opt, excluding/etc/bind/named.conf/etc/resolv.confwill be monitored by AIDE. - The following information will be included in the fingerprint: file permissions, link count, uid, gid, size ,selinux attributes and sha256 checksum.
The configuration should be reviewed and adjusted depending on gateway setup/application. For example by adding additional files to the monitored set and/or excluding files that might can change as part of normal device operation.
WarningIf ESF root directory and/or /etc are included in the monitored file set, it is necessary to reset the tamper status after ESF configuration changes, This can be done using the Security -> Tamper Detection section of ESF Web Console, REST APIs or MQTT requests.
In order to access the Security -> Tamper Detection section of ESF Web Console the kura.maintenance permission is required.
In order to use Tamper Detection REST APIs the rest.tamper.detection permission is required.
Startup check delay: The time to wait before performing the first action (either INIT or CHECK) after service activation or configuration update.
Startup check delay time unit: The time unit for the Startup check delay parameter.
Periodic check interval: The time interval between two consecutive periodic CHECK invocations after the first one.
Periodic check interval time unit: The time unit for the Periodic check interval parameter.
Diagnostics Service Integration
AIDE component supports sending alerts using the Diagnostics Service when it detects a change in the system integrity status.
Th service adds some configuration parameters to DiagnosticsService configuration to allow enabling/disabling Alert reporting and setting a custom alert code.
Updated 4 months ago
